
Introduction
The Switzerland-based ProtonMail end-to-end encrypted email service, launched in 2013, says on its website that it is "the world's largest secure email service with millions of users";[1] it also advertises itself as "NSA-proof."[2]
Labeled by Forbes as "the only email system the NSA can't access,"[3]ProtonMail is the latest technology to be adopted by jihadis for secure communications, including planning attacks, disseminating content, fundraising, and other purposes. It is gaining in popularity among jihadis, with vast potential for increased use by them and other extremists, particularly as the company's Terms of Service (TOS) do not prohibit such use of its platform[4] - even though it is, as ProtonMail itself openly acknowledged following the November 2015 Paris terror attacks, "on ISIS's list of recommended email providers."[5]
The company has made its position on encryption clear: Following the May 22, 2017 Manchester suicide bombing in which 22 people were killed and over 250 wounded, ProtonMail tweeted: "The #Manchester attack is a tragedy. However, compromising our freedom is not how we should confront terrorism."
Also, following the June 3, 2017 London Bridge attack, in which eight were killed and 48 wounded, ProtonMail CEO Andy Yen said, "Fighting terrorism does not translate into fighting internet freedom and security." ProtonMail's TOS states only: "By using this Service, you agree to not use this Service for any unlawful or prohibited activities."[6]
In January 2017, ProtonMail launched a Tor hidden service "to combat censorship and surveillance of ProtonMail users," noting that "it is simply not possible to run a privacy and security focused service in the US or in the UK."[7] In June 2017, the company announced the launch of ProtonVPN, a new VPN service, which it said was "to combat increased threats to online freedom," noting recent measures in the U.S. and U.K. and "the over 1.5 billion people around the world who live with censored Internet."[8] On August 16, 2017, ProtonMail introduced payment for its services in Bitcoin, in an announcement headlined "ProtonMail now includes Bitcoin support! You can now get secure email anonymously."[9]
As MEMRI has documented over the past few years (see landmark MEMRI report Encryption Technology Embraced By ISIS, Al-Qaeda, Other Jihadis Reaches New Level With Increased Dependence On Apps, Software - Kik, Surespot, Telegram, Wickr, Detekt, TOR: Part IV and others), encryption is becoming increasingly evident in terror cases - as illustrated in the U.S. Department of Justice's October 6, 2017 announcement of the unsealing of charges against three men for plotting terror attacks for ISIS in New York City in the summer of 2016. The charges stated that the men were"[c]ommunicating through Internet messaging applications" to allegedly plot to "conduct bombings and shootings in heavily populated areas of New York City" and that they "communicated, via electronic messaging applications accessible on cellphones."[10]
The following report focuses on ProtonMail's security features, statements by the company and its leadership about jihadis' use of its platform and its position on encryption, and how jihadis, including ISIS and its hacking and other groups, are utilizing it for communications, fundraising, and other purposes, and are recommending and promoting it on other platforms.
Security Features Of ProtonMail
ProtonMail is owned by Proton Technologies AG, which is headquartered in Geneva, Switzerland, with support centers in San Francisco, California, and Skopje, Macedonia. ProtonMail's CEO is Dr. Andy Yen.
 Dr. Andy Yen, ProtonMail CEO and founder. Source: protonmail.com/about
Dr. Andy Yen, ProtonMail CEO and founder. Source: protonmail.com/about
According to ProtonMail's website, it is the world's largest secure mail service providing end-to-end encryption, and has "zero access" to user data.[11] Its website states: "Data is encrypted on the client side using an encryption key that we do not have access to. This means we don't have the technical ability to decrypt your messages, and as a result, we are unable to hand your data over to third parties." It explains that "[b]y using open source libraries, we can guarantee that the encryption algorithms we are using do not have clandestinely built in back doors."[12]
The company says that it maintains its own server hardware at "several locations within Switzerland" so that user data never goes to the cloud. Its "primary datacenter," it says, is "located under 1000 meters of granite rock in a heavily guarded bunker which can survive a nuclear attack." The servers "utilize fully encrypted hard disks with multiple password layers so data security is preserved even if our hardware is seized." It adds: "We do not save any tracking information. By default, we do not record metadata such as the IP addresses used to log into accounts."[13]
An option it offers for emails is self-destructing encrypted messages: "You can set an optional expiration time on ProtonMail's encrypted emails, so they will be automatically deleted from the recipient's inbox once they have expired. This technology works for both emails sent to other ProtonMail users, and encrypted emails sent to non-ProtonMail email addresses."[14]
ProtonMail's "Transparency Report" With Details Of Requests For Data - Including On ISIS
On its website, ProtonMail also maintains a "Transparency Report," the "ProtonMail Warrant Canary," with information on requests to hand over data and to retain user data that it receives "on a daily basis," generally "legally binding court orders," requests from "foreign governmental entities," corporations, private individuals, and Internet security organizations. It states that it complies only with "legally binding requests that have been approved by a Swiss court." The "Transparency Report" lists 14 such requests, updated approximately once per month during 2017 and every few months during 2016.[15] Among these requests it lists:
- "In March 2017, we received a request from the Geneva prosecutor's office regarding a data request from overseas that came with a valid International Letters Rogatory. The request came from the German government, investigating an account with links to ISIS. However, we were unable to provide the data requested by the German government as we did not have access to the data requested.
- "In April 2017, we received a request from the Swiss Federal Police about an information request coming from a former Soviet republic (not Russia) regarding a case with an immediate threat of bodily harm to innocent civilians. Proton Technologies AG decided to comply immediately with the data request, to the extent that it is possible, given our cryptography, with the understanding that a valid Swiss court order will be immediately delivered to our office as soon as possible."[16]
While the company, and its CEO Yen himself, are naturally motivated by economic reward, their emphasis that ProtonMail complies with requests for information from democratic Western governments only if they are "legally binding" and "have been approved by a Swiss court" indicates that the Swiss government is creating a hub of neutrality where terrorists and other criminal actors can freely operate - like the hub of neutrality that it made available to the Nazi regime in Germany during World War II.
Drawing a false parallel between banning terror activity on his platform and outlawing democracy, Yen presents himself and his company as the sole defenders of freedom - even against democratically elected governments and constitutionally established courts in those democracies. This duplicity is clearly manifested in: a) his expressions of sympathy for the victims of terrorism while continuing to provide terrorists with an essential tool for their crimes, and b) ProtonMail's violation of its own Terms of Service - which oblige the user to "agree to not use this Service for any unlawful or prohibited activities"[17] - by failing to enforce them.
ProtonMail "Shocked And Horrified" At November 2015 Paris Attacks, "Greatly Saddened" To Learn It's Recommended By ISIS - But Calls Bans On Encryption "Politically Convenient"; "Privacy Is A Fundamental Human Right"
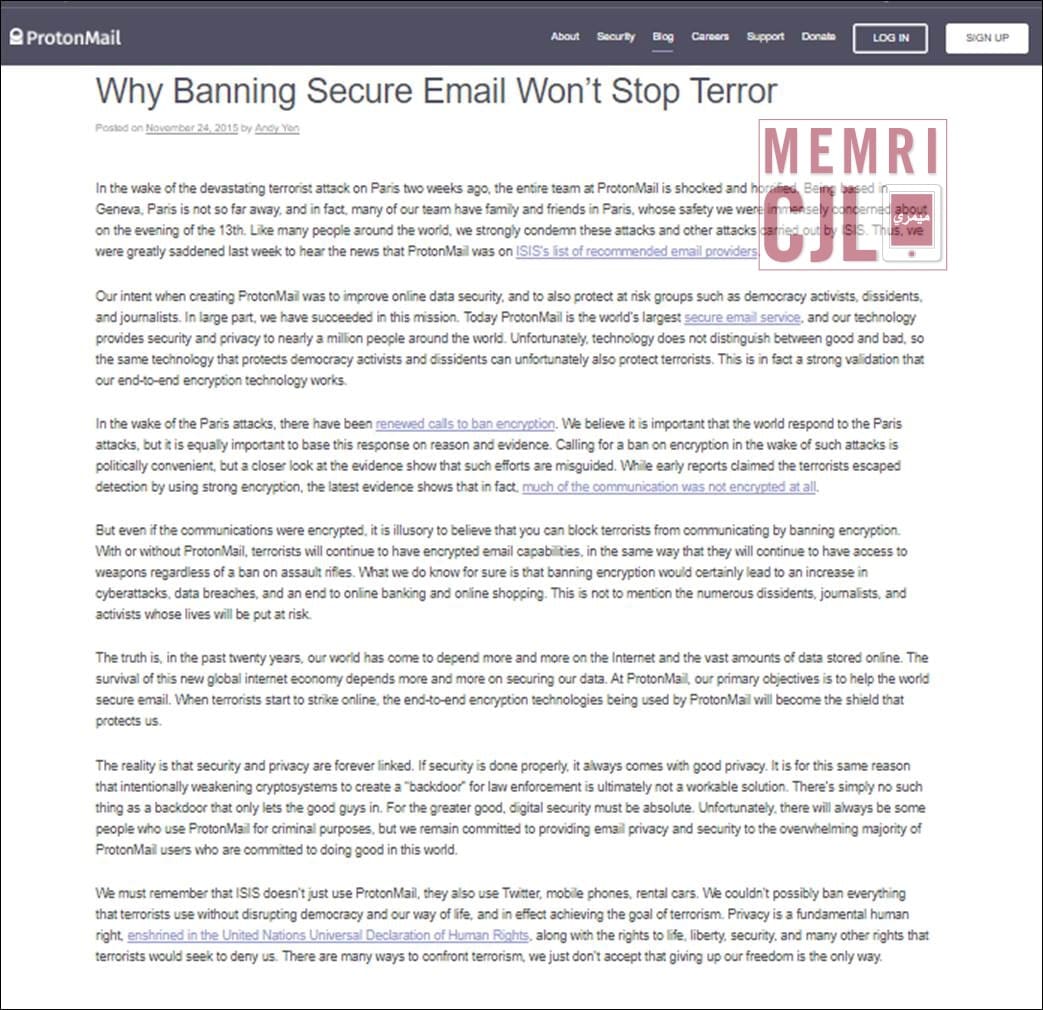
Proton has been very open on its views about online freedom of speech and on its objections to any restrictions or access to encryption. Following the November 13, 2015 Paris attacks, as legislators and law enforcement were pushing for creating "backdoors" in encrypted communications, ProtonMail posted a statement by CEO Yen on its website titled "Why Banning Secure Email Won't Stop Terror" on the company website. It stated:
"In the wake of the devastating terrorist attack on Paris two weeks ago, the entire team at ProtonMail is shocked and horrified... Like many people around the world, we strongly condemn these attacks and other attacks carried out by ISIS. Thus, we were greatly saddened last week to hear the news that ProtonMail was on ISIS's list of recommended email providers.
"Our intent when creating ProtonMail was to improve online data security, and to also protect at risk groups such as democracy activists, dissidents, and journalists. In large part, we have succeeded in this mission. Today ProtonMail is the world's largest secure email service, and our technology provides security and privacy to nearly a million people around the world. Unfortunately, technology does not distinguish between good and bad, so the same technology that protects democracy activists and dissidents can unfortunately also protect terrorists...

"In the wake of the Paris attacks, there have been renewed calls to ban encryption. We believe it is important that the world respond to the Paris attacks, but it is equally important to base this response on reason and evidence. Calling for a ban on encryption in the wake of such attacks is politically convenient, but... such efforts are misguided. While early reports claimed the terrorists escaped detection by using strong encryption, the latest evidence shows that in fact, much of the communication was not encrypted at all...
"[I]t is illusory to believe that you can block terrorists from communicating by banning encryption... [S]ecurity and privacy are forever linked. If security is done properly, it always comes with good privacy. It is for this same reason that intentionally weakening cryptosystems to create a 'backdoor' for law enforcement is ultimately not a workable solution... [T]here will always be some people who use ProtonMail for criminal purposes, but we remain committed to providing email privacy and security to the overwhelming majority of ProtonMail users who are committed to doing good in this world...
"ISIS doesn't just use ProtonMail, they also use Twitter, mobile phones, rental cars. We couldn't possibly ban everything that terrorists use without disrupting democracy and our way of life, and in effect achieving the goal of terrorism. Privacy is a fundamental human right... There are many ways to confront terrorism, we just don't accept that giving up our freedom is the only way."[18]
 Source: Protonmail.com/blog/privacy-encryption-and-terrorism/, accessed September 25, 2017.
Source: Protonmail.com/blog/privacy-encryption-and-terrorism/, accessed September 25, 2017.
ProtonMail Reacts To May 22, 2017 Manchester Bombing: "Compromising Our Freedom Is Not How We Should Confront Terrorism"
On May 26, 2017, four days after the May 22 Manchester suicide bombing in which 22 people were killed and over 250 wounded, ProtonMail tweeted: "The #Manchester attack is a tragedy. However, compromising our freedom is not how we should confront terrorism." The tweet linked to an media report on an expected UK government crackdown on encrypted messaging apps.

ProtonMail CEO Reacts To June 3, 2017 London Attack
Following the June 3, 2017 London Bridge attack, in which eight were killed and 48 wounded, and UK Prime Minister Theresa May's subsequent call for more to be done to "regulate cyberspace to prevent the spread of extremism and terrorist planning," Protonmail CEO Andy Yen was quoted by the UK technology website The Register as saying: "Fighting terrorism does not translate into fighting internet freedom and security... Even if Prime Minister Theresa May's request is pushed by a good intention, asking tech companies to create backdoors for governments goes against the basic rule of cybersecurity. It's impossible to have backdoors serving only the 'good guys,' which is the reason why for the greater good, digital security must be absolute."[19]
Jihadis, Including ISIS, Use ProtonMail - And Promote It On Other Platforms
The following are examples of how jihadis on platforms such as Telegram are promoting the use of ProtonMail.
U.S.-Designated Foreign Terrorist Organization Tehreek-e-Taliban - Pakistani Taliban - Provides Its ProtonMail Address To Readers
One of the most recent examples of ProtonMail's use by jihadis was on October 18, 2017, when the U.S.-designated Foreign Terrorist Organization Tehreek-e-Taliban Pakistan - the Pakistani Taliban - provided its ProtonMail address on promotional material for the release of the second issue of its English-language online magazine, Sunnat E Khaula. The magazine is aimed at women and encourages them to participate in jihad; this issue states: "We strive to provoke the sisters to embark on hijra, we strive to provoke the sisters to take up jihad, follow the footsteps of Hazrat Khaula r.a. and firmly stand by the side of the mujahideen in Islam."[20]
 Pro-ISIS United Cyber Caliphate (UCC) Uses ProtonMail
Pro-ISIS United Cyber Caliphate (UCC) Uses ProtonMail
In a post on Telegram that included the video "A message to all Muslim Hackers," the United Cyber Caliphate provided their contact information as a private ProtonMail account.
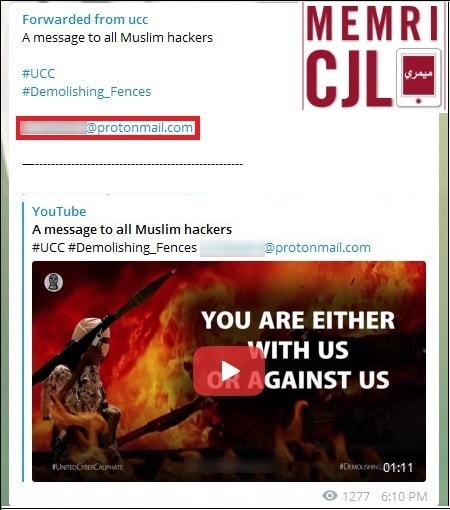
UCC Appeal For Graphic Designers, Banner Makers, Tweeters, News Disseminators Asks Them To Contact Group Via ProtonMail
ISIS supporters on Telegram circulated a request from United Cyber Caliphate (UCC) for graphic designers, banner makers, tweeters, and news disseminators. The request specified that interested individuals contact UCC at a ProtonMail address.

Latest Posts



