On November 25, 2015, the Pro-ISIS online jihadi group Cyber Kahilafah launched its official channel on the encrypted messaging app Telegram. Posts on Cyber Kahilafah's channel include: pro-ISIS , information on how to circumvent online surveillance, a link to reportedly hacked NASA data, and plans of future cyber-attacks. Cyber Kahilafah's Telegram channel also highlights Twitter's campaign to target cyber jihadi organizations, including Cyber Kahilafah itself. This channel utilizes various digital content sharing platforms including: Sendvid, Google Drive, Twitter, and Justpaste.it. Cyber Kahilafah' channel also highlights the use of TOR, a software platform allowing for online anonymous communication. The variety of platforms underscores the resourcefulness of global jihadist organizations in the digital sphere.
On November 27, 2015, Cyber Kahilafah posted IP addresses belonging to "enemies of the [Islamic] State who launch spam campaigns against its supporters." Cyber Kahilafah also posted a password to access the IP list on a Ghostbin. account. Ghostbin is a secured website that provides encryption and expiration of information shared online. The hacktivist organization Anonymous has also made use of Ghostbin as a resource for the dissemination of sensitive information.
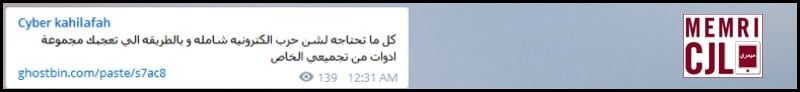
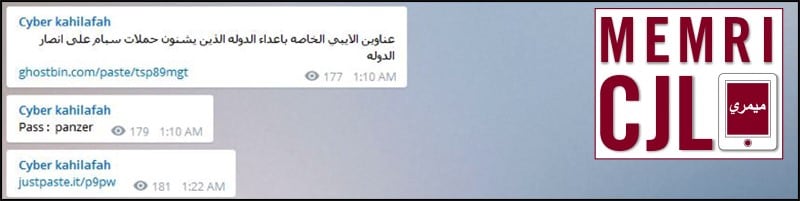 Cyber Kahilafah link to IP addresses and password to the encrypted sharing service Ghostbin.
Cyber Kahilafah link to IP addresses and password to the encrypted sharing service Ghostbin.
Using the private instant video uploader, Sendvid, Cyber Kahilafah uploaded a pro-ISIS video on November 28, 2015.
On December 2, 2016, Cyber Kahilafah instructed followers to use the Orbot package which runs TOR on Android products.

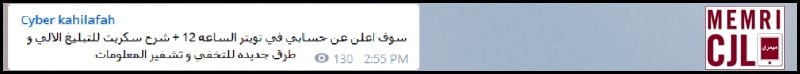
On December 22, 2015, Cyber Kahilafah advertised that it will publish new methods for the encryption of information.
Cyber Kahilafah published a list of reportedly pro-ISIS websites on December 30, 2015. The list was originally published on Pastebin with the hashtag #OpISIS. Cyber Kahilafah appeared to mock the efforts of #OpISIS, an Anonymous related campaign to take down ISIS related sites and accounts.

On January 3, 2016, Cyber Kahilafah published a video with cartoon animation as well as step by step instruction on the making of an Improvised Explosive Device (IED).
 A day prior on January 2, 2016, Cyber Kahilafah published a Google Drive link regarding the making of IEDs.
A day prior on January 2, 2016, Cyber Kahilafah published a Google Drive link regarding the making of IEDs.
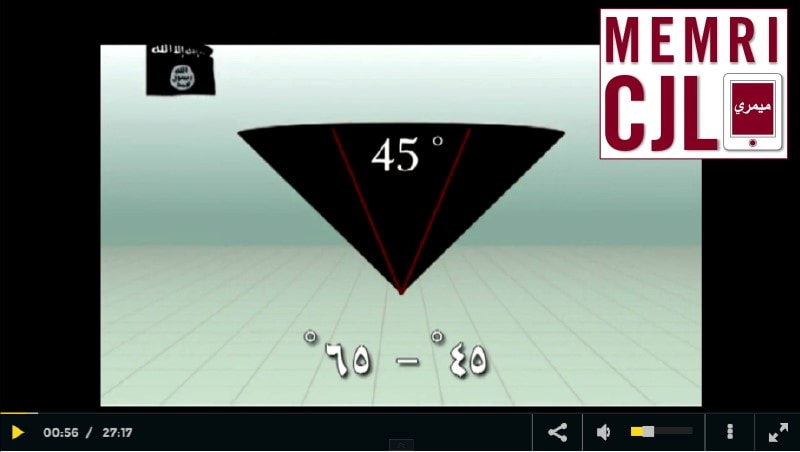
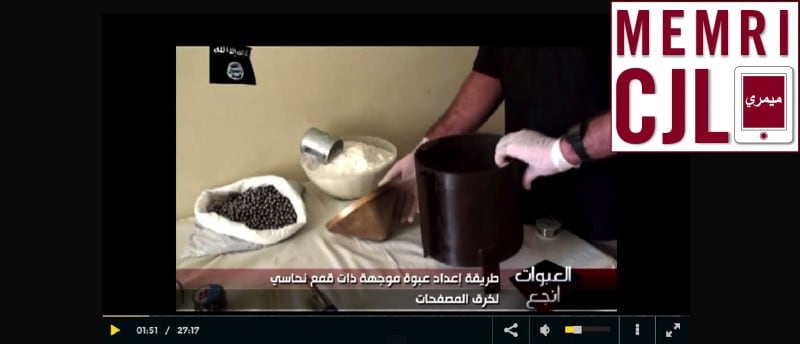 Cyber Kahilafah published a video with instructions to build an IED.
Cyber Kahilafah published a video with instructions to build an IED.
 Cyber Kahilafah noted that this video is especially useful for the "Love Wolves" in the Arabian Peninsula.
Cyber Kahilafah noted that this video is especially useful for the "Love Wolves" in the Arabian Peninsula.
Cyber Kahilafah informed followers that its Twitter account had been taken down on January 5, 2016.
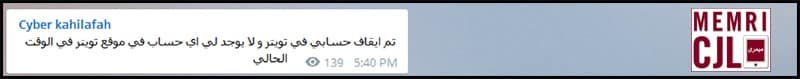
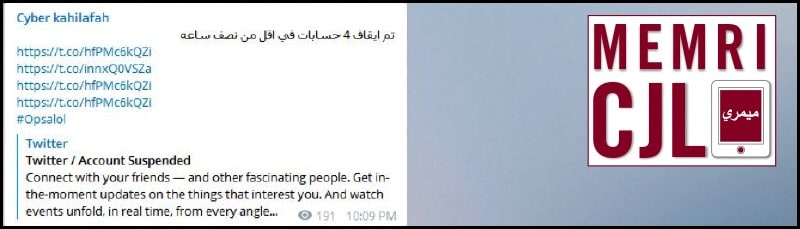 Previously, on November 27, 2015 Cyber Kahilafah announced that four Twitter accounts it ran were deleted within less than half an hour.
Previously, on November 27, 2015 Cyber Kahilafah announced that four Twitter accounts it ran were deleted within less than half an hour.
 Message from Twitter following Cyber Kahilafah's suspended links.
Message from Twitter following Cyber Kahilafah's suspended links.
![]() In the Twitter Rules page Twitter maintains a rule specifically against the threatening or promotion of terrorism.
In the Twitter Rules page Twitter maintains a rule specifically against the threatening or promotion of terrorism.
On February 4, 2016 Cyber Kahilafah posted a link with apparently hacked NASA information. The Cyber Kahilafah post follows January 2016 reports that 250 gigabytes of NASA data was hacked on behalf of the group AnonSec. Information is reported to include flight logs, radar logs, video taken from NASA aircraft, and employee information including names, addresses, and phone numbers.
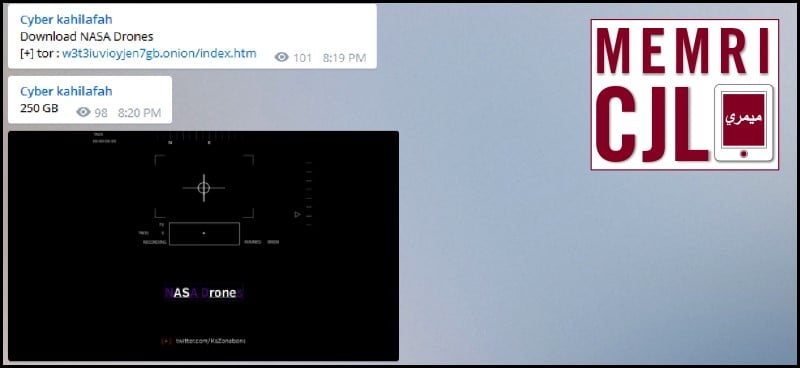 Cyber Kahilafah claimed 250 gigabytes as the file size, the amount indicated in the January 2016 in the NASA breach.
Cyber Kahilafah claimed 250 gigabytes as the file size, the amount indicated in the January 2016 in the NASA breach.
February 16, 2016 Cyber Kahilafah advertised tools for engaging in electronic warfare, hosted on the encrypted sharing service Ghostbin.
Cyber Kahilafah suggested on February 17, 2016 that its followers view a specific Twitter account, which had a post supposedly on botnets.
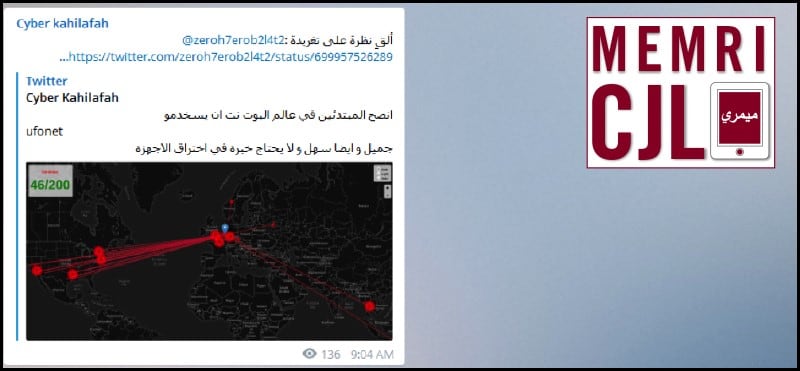 The Twitter account @zeroh8erob2l4t2 has subsequently been removed from the Twitter, likely to terrorist related activities.
The Twitter account @zeroh8erob2l4t2 has subsequently been removed from the Twitter, likely to terrorist related activities.
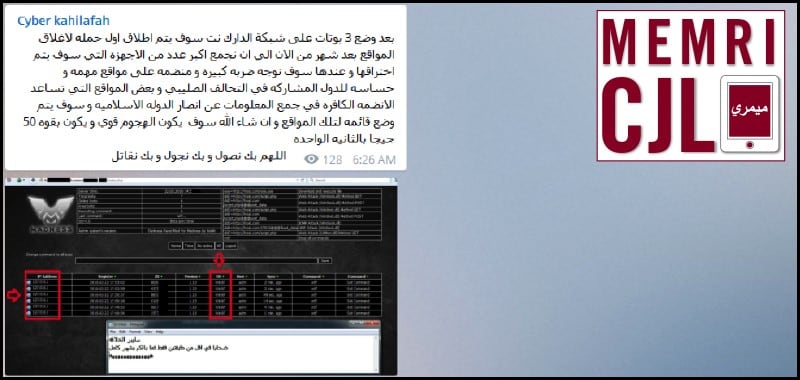
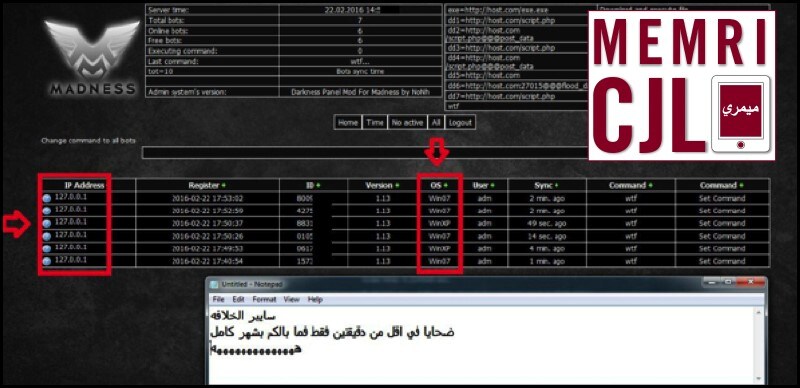
On February 22, 2016 Cyber Kahilafah discussed planting "bots" on the "Dark Net" and a planned cyber-attack. The cyber-attack is to be directed towards sites of those countries participating in the "Crusader Alliance," the anti-ISIS military campaign. Cyber Kahilafah also stated the technical strength of the attack, which is said to take place at a strength of 50 gigabytes per second.
Latest Posts



